
Voice security technology can be easily inserted into most applications because most applications have embedded processors. This is important because most consumer products must provide the most features for the lowest cost. Adding additional hardware can sometimes make your product noncompetitive. Cellular phone technology is an example of such an application.
The diagram below shows the basic hardware used in voice security. The user's voice is read into the embedded processor through a microphone and an analog-to-digital converter (ADC). The embedded processor transforms the user's voice into templates that can be compared with previously recorded templates of the user's voice. If the voice security test is passed, the embedded processor enables the product to function. If the voice security test is failed, an indicator (visual or verbal) tells the user to try again.
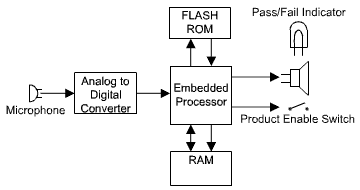
Figure 1: Required Voice Security Hardware
A cell phone has all of the needed functions given above. All they lack is the voice security algorithm to run on their hardware!
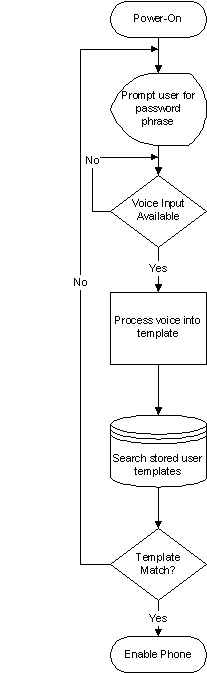
There are several ways that the voice security algorithm could be implemented on a cell phone. One method is to use a power-on enabling function similar to what exists in phones today. Current phones have a security feature when the customer turns on the phone they must enter a Personal Identification Number (PIN) to enable the phone. Instead of a PIN, the embedded processor's program could be modified to implement the voice security algorithm as shown below.
During power-up sequences, the amount of processing done by the embedded processor is minimal. Most of the time is spent waiting for user input such as keypad entry for the PIN. This time could be used instead to prompt the user for a voice password and monitor the microphone to capture the voice input. Upon receiving the voice input, the embedded processor transforms the data input into a voice template for comparison against the user database. Even the smallest of embedded processors can perform this transform in a time-effective manner to prevent the user from excessive waits during voice validation. If the voice template matches, the phone is then enabled. If the voice template does not match, the user can try again. All this can be done on the embedded processor that is usually not fully loaded during this time.
This application only adds about 4-8 Kbytes of new code to the product. Considering cell phones have games and other toys running on the embedded processor, this will not require any additional parts to be added to the phone.
Voice Security Systems Inc.
Biometric Technology Licensing
24591 Seth Circle, Dana Point, CA 92629
Phone: +1 949
493-4030
E mail: info@voice-security.com
Privacy Notice | Conditions of Use
FreeKey® and Voice Protect® are registered trademarks of Voice Security
Systems Inc.
Copyright © 1999- Voice Security
Systems Inc.
All Rights Reserved.