Voice Security Systems, Inc.
The Voice of Choice"New Voice" Technology
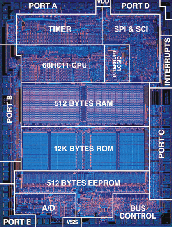 |
Voice Security Systems, Inc. pioneered methods of speaker verification that can effectively operate without the benefit of an external server or hard drive. The entire software program and templates can be operated and stored in the protected device itself. Optionally, the voice templates used for validation can be loaded at verification time from a smart-card or stored in external RAM due to their small size. The greatest benefit of our method is that user security can be self-contained within a device. Cell Phones, ATM cards, Automobiles and Door Access are just some of the applications that are protected by FreeKey® / Voice Protect® technology. |
 |
 |
Other speaker verification technologies may rely on costly database management of many user's templates, and in some cases risk sending the biometric data or even the voice stream itself over phone lines, air waves, or Internet lines. FreeKey® / Voice Protect® technology ensures that the biometric data stays safe as the spoken phrase cannot be reconstructed from the "key" created by the user. For cloud based applications, the user's "voice prints" can be contained in a single, encrypted IP packet in as little as 780 Bytes in size. Voice Security Systems technology can deliver biometric security with selective, always-on command and control to the market at a lower cost than anyone else in the industry, with no re-occurring maintenance costs such as database management or complicated user training. Once the FreeKey® / Voice Protect® technology is built into a product it will continue to function independently for the life of the product. |